🔑 Encryption vs 🔒 Hashing
-
:key: Encryption vs :shield: Hashing
Introduction
EncryptionandHashing. The two main terms incryptogrphy. We know both techniques are using to hide actual data in programming. But there are few major differences between.Let's see the very basic concept & difference between Encryption and Hashing.
Encryption
Encryption is the process of using an algorithm to transform information to make it unreadable for unauthorized users. - Techopedia
Encryptionis a kind of algorithm to transform the data to unreadable format or specific format that can't be read by anyone else.It looks like,
Before Encrypt - Hi, How are you?
After Encrypt - dahj963hqd92h2hr2f hf9vb3y9863b52c3569Only the
systemorspecific usercan decrypt the data.The lenth of encrypted data depends on the actual data lenth. If you input small data, the encrypted data also will be smaller. If you input huge data, the encrypted data will be larger.
The encryption machanism has two type of keys.
1. Public Key - Open key that use to encrypt data.
2. Private Key - Secret key that use to decrypt the encrypted data.
Hashing
Hashingis also working likeencryption. ButHashdoesn't have keys likepublic&private.And Also,
Hashing's output doesn't depends on the input size. Its' output will be a fixed size of string.It means, imagine the hashing function
hash()returns 32 characters output, The output will not be increased or decresed.echo hash('a') 0cc175b9c0f1b6a831c399e269772661 //32 chars output echo hash('Data encryption translates data into another form, or code, so that only people with access to a secret key (formally called a decryption key) or password can read it. Encrypted data is commonly referred to as ciphertext, while unencrypted data is called plaintext. Currently, encryption is one of the most popular and effective data security methods used by organizations. Two main types of data encryption exist - asymmetric encryption, also known as public-key encryption, and symmetric encryption') fc2a2d702e1af572e4fe4dddb31ccc90 //32 chars output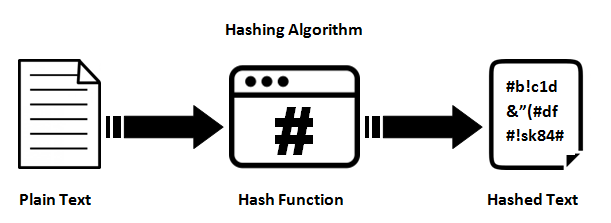
The another thing is, We can't reverse the hash. It means we
canhash a data. But wecan'tget data again from hash.
Encryption Hashing Output length not Fixed Fixed Output length Can retrieve data again Can't retrieve data again Use as a trusted data Use as a trusted and unique identifier
When use Encryption and Hashing ?
Use cases of
hashing,- Store Passwords in Database.
- Compare file hashes for check damage (Check Sum).
- Compare data for difference or changes.
Use case of
encryption,- Store sensitive data.
- Transfer data over network / internet.
- Make dedicated file system / extensions.
Thank you!
With :hearts: B6.
-
Good explanation, keep posting good luck
-
Nice Work! Keep up!
-
good work bro.. lankadevelopers are making a huge IT world in Sri Lanka
-
@lkdev Thank you for your support :)
-
@lahirunc Thanks bro
-
@root Yes. The srilanka's stack overflow :)
-
nice explanation bro...
-
@dev_lak Thank you bro
-
cool explanation broh 🎩
-
@MoRaL Thank you bro
-
Good post
-
@isuru2014 Thx Bro